All internet traffic, to and from Greyman Network servers and users is done through HTTPS. We do not support or allow unencrypted, plain text traffic through our systems, as it could be a security risk for us and our users. In addition to encrypting the network traffic between users and the servers, the messages within may also be encrypted, end to end, in private rooms (required) or in public rooms (optional, but not recommended. See why public rooms aren’t encrypted).
HTTPS stands for Hyper Text Transfer Protocol Secure. It is a protocol used for securing the communication between two systems. In this case, between you, the user, and the Greyman Network servers.
The following figure illustrates the difference between an un-secure communication over HTTP, and a secure communication over HTTPS:
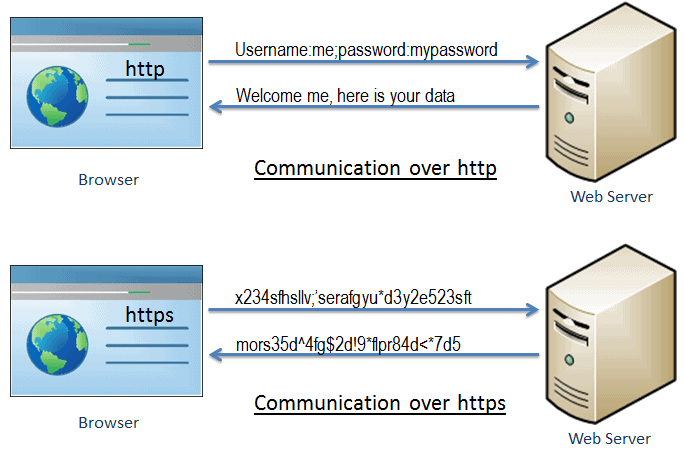
As you can see in the figure above, HTTP data transfers the data in a plain, unencrypted text format, so anyone along the communication path can see the contents of the packet. Furthermore, HTTPS transfers the data in the encrypted format, thus preventing anyone from reading or modifying the data during the transmission. Even if someone manages to intercept the communication, they will not be able to use it due to the encryption.
As mentioned in the Overview, all internet traffic between users and Greyman Network servers is forced to go through HTTPS. Therefore, there is always a layer of encryption taking place, and only the users and the server are able to understand the communication, as only they have the proper keys for decryption.
Greyman Network has two different types of rooms, public and private. Public rooms are typically unencrypted, and private rooms are required to use end to end encryption.
As mentioned above, in What is HTTPS?, all the data transmission to and from the server is encrypted, but this section will talk about the second layer of encryption that can take place here, on the actual room messages (text, images, video, etc.) themselves.
The following figure illustrates how end to end encryption works in these rooms:
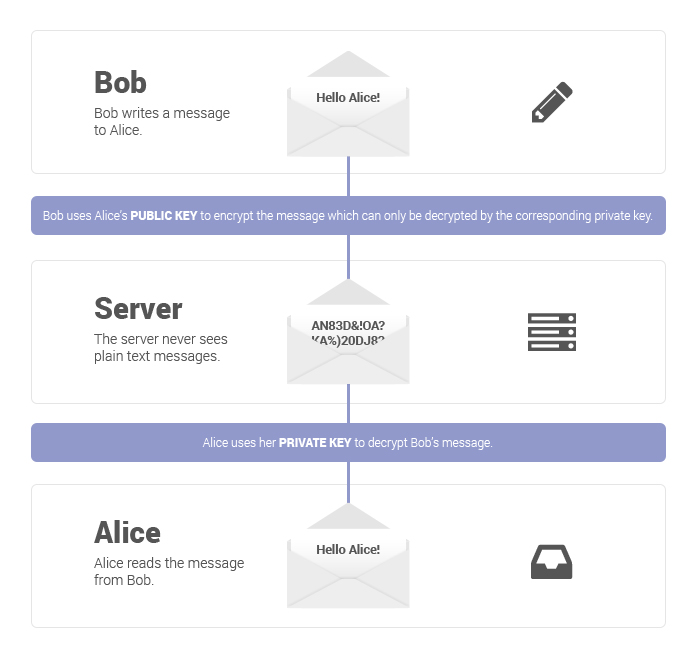
As you can see in the figure above, Bob and Alice both have a keys that can encrypt and decrypt messages, and only they have the keys. Bob encrypts the message using Alice’s public key and sends the message through the Greyman Network server, which is then forwarded to Alice. Alice has a private key that is able to decrypt messages from Bob. In this instance, the server stores the encrypted messages and is unable to read any of the message sent. The only way to gain access to the message is to be in the room or have the keys from Bob or Alice.
There is no value in encrypting public rooms. If anyone can join the room, then encryption does not protect the contents, and may offer inconvenience for some users. In addition to that, encrypting messages does take additional processing power and can slow down the server during times of high activity.
For public rooms, to support searching and history, the server stores all the activity and messages in the public rooms.
For private rooms, the server stores all the activity and messages, but in its fully encrypted form. Searching will not work for private, encrypted rooms, as the server doesn’t have access to read the messages, and therefore is unable to search them.
If a server is compromised, whether it be physically compromised, hacked, or seized by authorities, the only information that will be able to be retrieved from the server will be the information shown above in What data does the server store?. The private rooms, as they are encrypted from user to user, and stored in its encrypted format on the server, will yield no information to them. The public rooms will show the same information that you could get by joining the server and joining the room yourself, and therefore provides no reward for compromising the server.
